Hi!Harmony!-复现
一看题目是鸿蒙联想到鸿蒙操作系统
不过之前没做过这一方面的题目
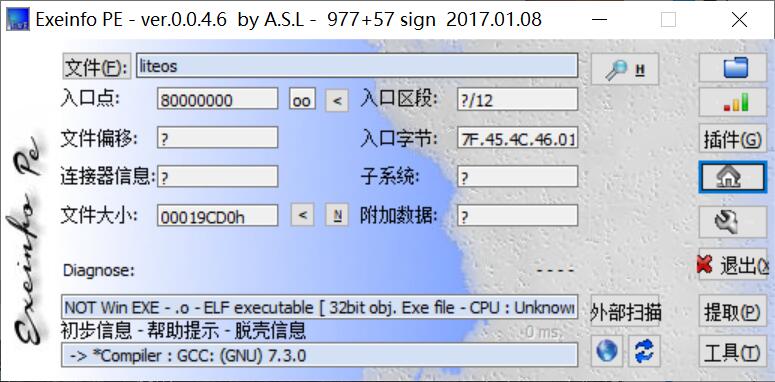
文件丢进EXEinfos里面看看文件信息
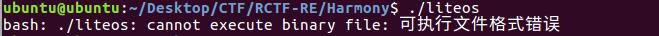
用Ubuntu打开看看,发现也不太行
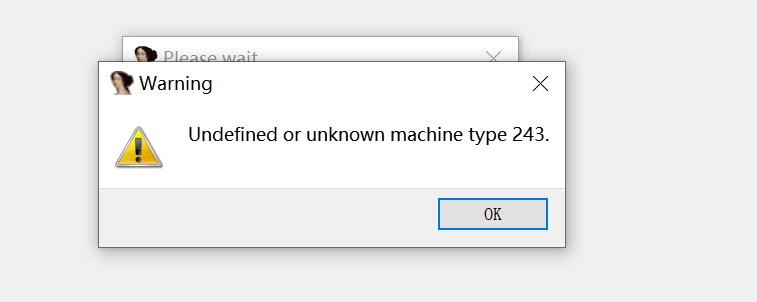
准备用IDA静态分析 发现IDA打不开
用file命令查看下文件信息
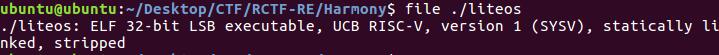
看到了一个信息RISC-V 百度搜索下
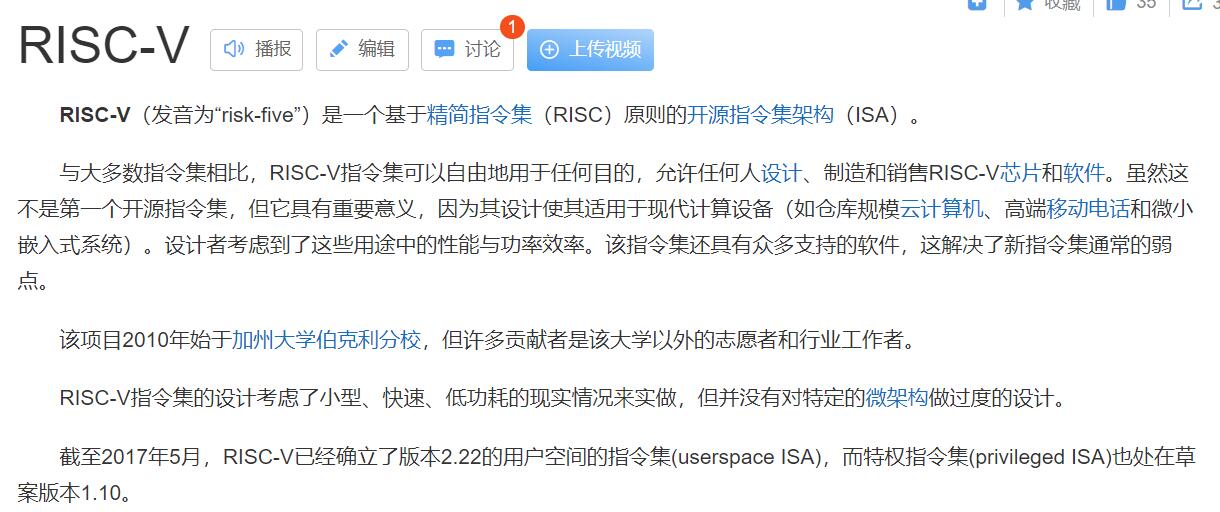
一个指令集 怪不得IDA打开 搜下有没有关于IDA的RISC-V的插件https://github.com/shuffle2/riscv-ida
经过一大堆艰难的操作发现 不能F5。。。。。。。
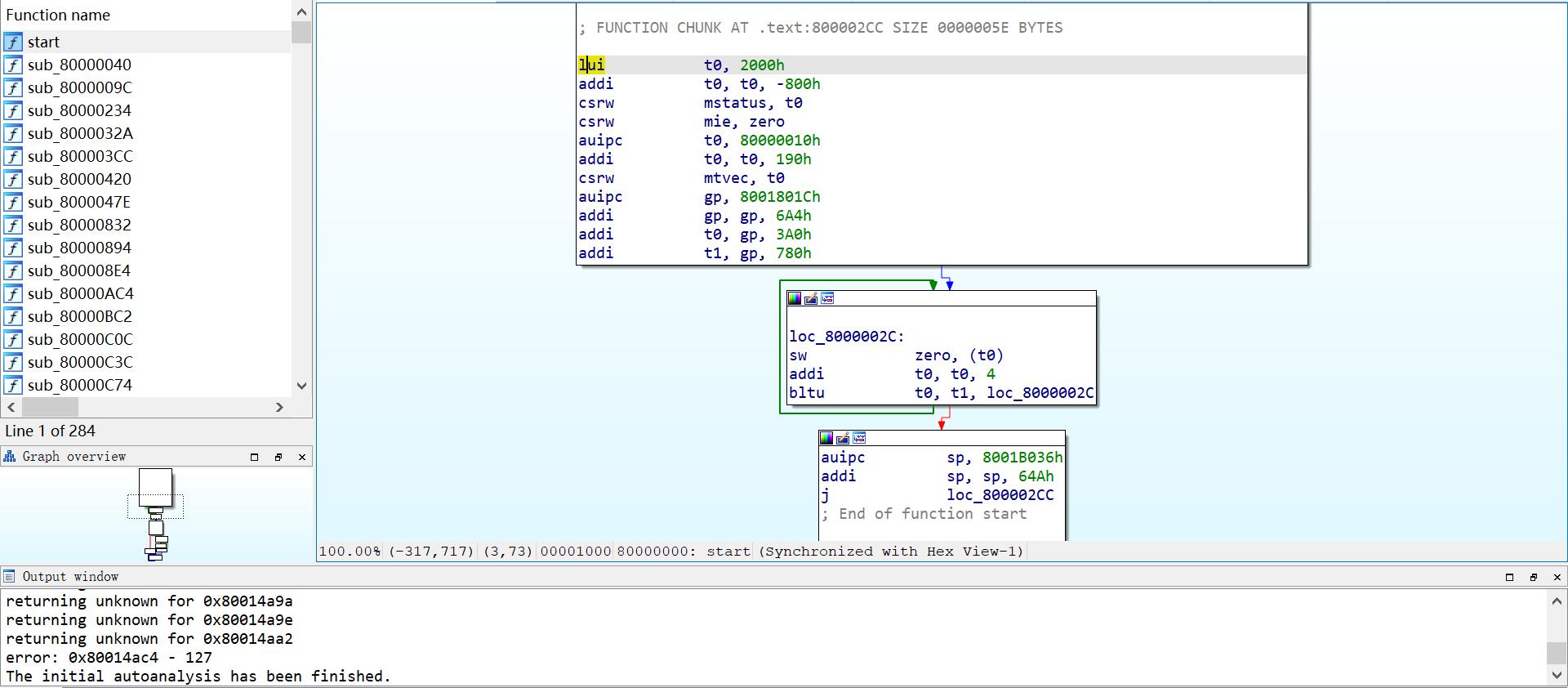
总不能硬读汇编把 没学过这个架构 搜索其他脚本也报错 这也是为啥我再比赛过程中没做出该题的原因
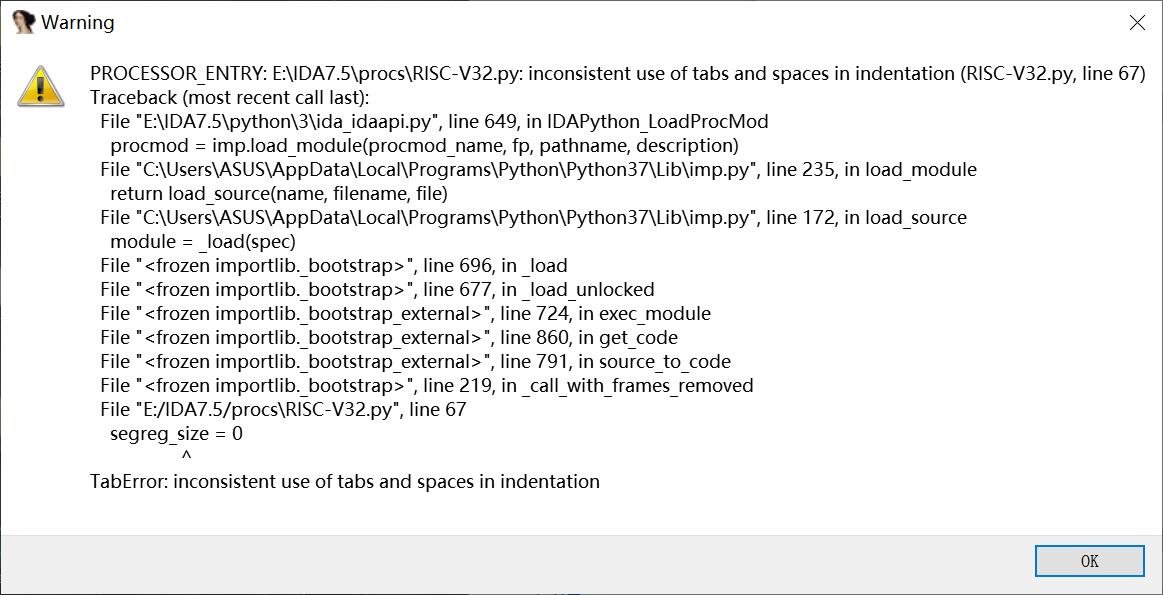
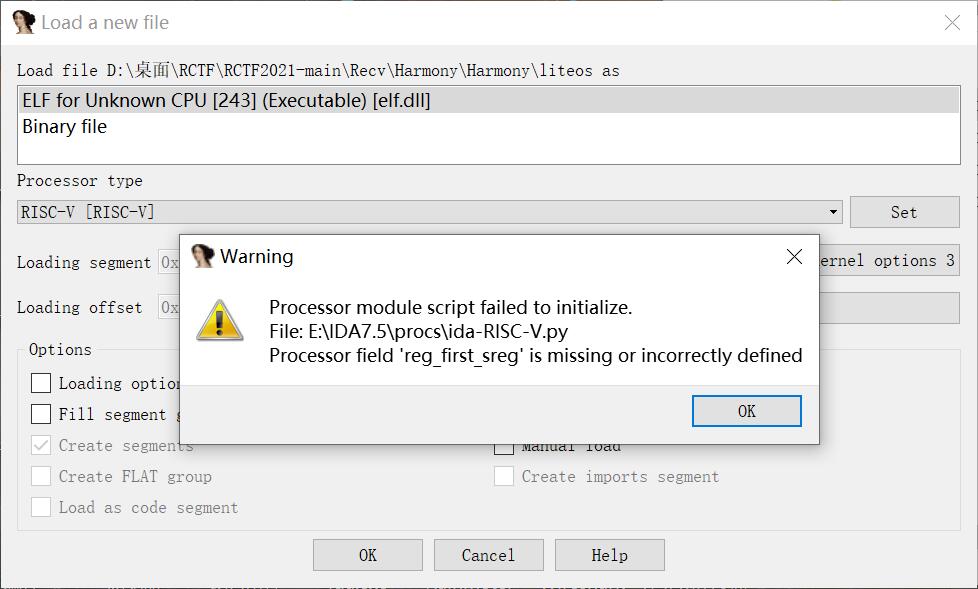
后面想想用新学习到的Ghidra试试 发现还真的可以 不得不说这个反编译工具还是强啊
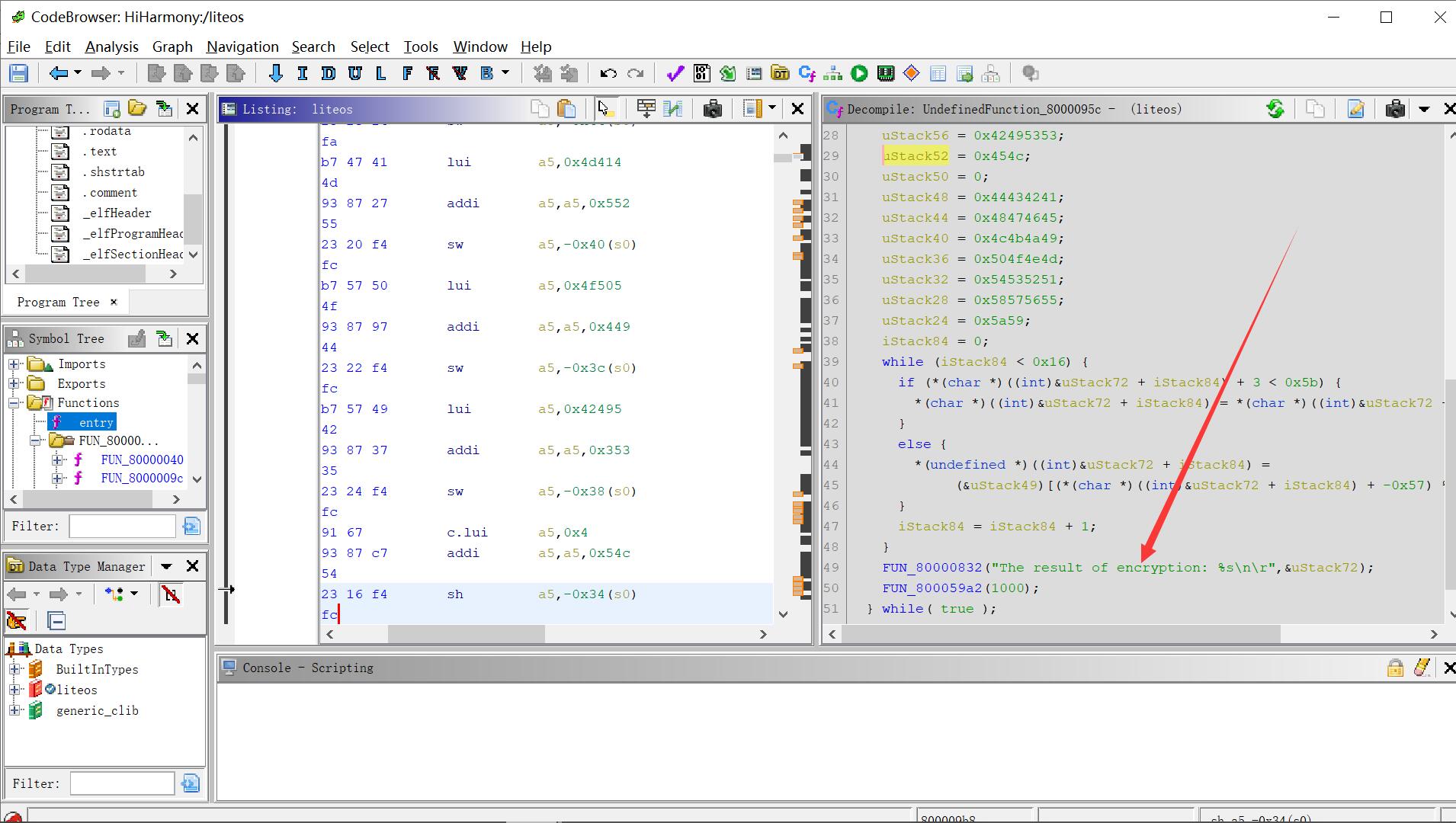
反编译伪代码 —解密模块
1 |
|
注意因为数据是小端存储 所以提取出来要稍加注意
EXP
1 | data1 = [0x48,0x41,0x52,0x4d,0x4f,0x4e,0x59,0x44, |